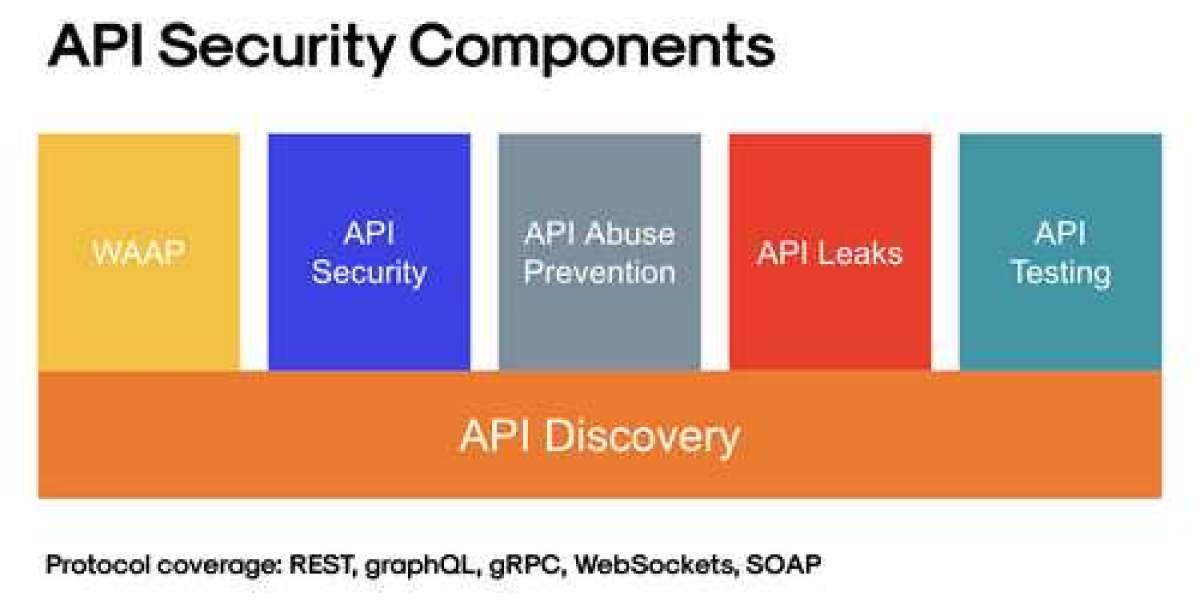
In the ever-evolving landscape of digital communication, Application Programming Interfaces (APIs) serve as the linchpin for seamless interaction between software systems. However, with this connectivity comes the pressing need for robust API security measures to protect sensitive data and maintain trust among users and systems alike.
What is API Security?
API security encompasses a comprehensive set of practices and protocols aimed at fortifying APIs against unauthorized access and malicious attacks. It involves implementing authentication mechanisms, encryption techniques, and real-time monitoring to ensure the integrity and confidentiality of data transmission. At its core, API security is about safeguarding the flow of information between applications, preventing breaches, and preserving the sanctity of digital interactions.
Key Aspects of API Security:
Authentication and Authorization: Implementing strong authentication methods, such as OAuth and API keys, is fundamental in verifying the identity of users and applications. By granting access only to authorized entities, organizations can mitigate the risk of unauthorized access and data breaches.
Encryption and Data Protection: Employing encryption protocols like Transport Layer Security (TLS) encrypts data during transmission, thwarting attempts by malicious actors to intercept sensitive information. Encryption acts as a shield, ensuring that data remains confidential and secure throughout its journey across networks.
Web API Security: Web APIs, particularly those exposed to the internet, are susceptible to a myriad of attacks if not adequately protected. Measures such as input validation, parameterized queries, and output encoding are imperative in thwarting common vulnerabilities like SQL injection and cross-site scripting (XSS). Additionally, implementing firewalls and intrusion detection systems adds an extra layer of defense against malicious exploits.

- Role-Based Access Controls: Implementing access controls based on roles and permissions ensures that users only have access to the resources they need, minimizing the risk of unauthorized data exposure.
- Regular Security Audits: Conducting regular security audits and penetration testing helps identify vulnerabilities and weaknesses in the API infrastructure, enabling organizations to address them proactively.
- Compliance with Standards: Adhering to industry standards such as OAuth and OpenID Connect, along with regulatory requirements like GDPR and HIPAA, demonstrates a commitment to safeguarding user information and maintaining trust.
In conclusion, API security is paramount in the digital ecosystem, where the seamless exchange of data drives innovation and collaboration. By implementing robust security measures and adhering to best practices and standards, organizations can mitigate risks, protect sensitive information, and foster trust among users and stakeholders. Prioritizing API protection ensures the reliability and security of digital interactions, paving the way for a resilient and secure digital future.